Enterprise-Grade Security for AI Systems You Can Trust
Security isn't a checkbox. It's our foundation. Every layer of Docmet's architecture is designed to protect your most sensitive knowledge. When you deploy AI in enterprise environments, you're not just processing data—you're handling trade secrets, customer information, and strategic assets. Docmet's security architecture ensures your knowledge stays protected, compliant, and completely under your control.

SECURITY OVERVIEW
Built on Zero-Trust Principles:
In traditional systems, security is an afterthought—a firewall around the perimeter with soft interiors. Docmet inverts this model. We assume breach and design every component with defense-in-depth.
Our Security Philosophy:
- Assume No Trust
- Every request is authenticated and authorized, even from internal services. No implicit trust based on network location.
- Verify Continuously
- Authentication isn't a one-time event. Session validation, token refresh, and behavior monitoring happen continuously.
- Minimize Blast Radius
- Tenant isolation, role-based access, and data compartmentalization ensure that even in worst-case scenarios, exposure is limited.
- Full Transparency
- Complete audit trails for every action. You always know who accessed what, when, and why.
Why Generic AI Tools Fall Short:
Enterprise AI introduces unique security challenges that consumer AI tools weren't designed to address.
- Challenge 1: Data Leakage to Public Models:
- The Risk: Employees paste sensitive data into ChatGPT, Claude, or public AI tools, unknowingly transmitting trade secrets to third-party servers. Data may be retained, logged, or used for model training.
- Real Impact:
- Samsung engineers leaked proprietary code to ChatGPT
- Law firms exposed client privileged communications
- Healthcare providers sent PHI to public AI services
- Docmet's Solution: Zero data sent to public APIs without explicit authorization. All processing happens within your deployment environment with contractual DPAs in place.
- Challenge 2: Insufficient Access Control:
- The Risk: Traditional document systems have coarse permissions (view/edit entire folder). AI search can surface documents users shouldn't access. "Search all contracts" might reveal executive compensation or M&A plans to unauthorized employees.
- Real Impact:
- Junior employees accessing board-level strategic documents
- Contractors viewing confidential HR information
- Cross-department information leakage
- Docmet's Solution: Granular RBAC at User/Team/Role/Space/Folder/Page level. AI respects all existing permissions—if you can't see a document, the AI can't retrieve it for you.
- Challenge 3: No Audit Trail of AI Decisions:
- The Risk: When AI makes recommendations ("Approve this budget"), there's no record of WHY. Compliance auditors need full provenance: what data was accessed, what logic was applied, who approved.
- Real Impact:
- Failed regulatory audits due to inability to explain AI decisions
- Legal liability from opaque AI recommendations
- No accountability for AI-assisted actions
- Docmet's Solution: Complete reasoning traces logged for every query. See exactly which documents were retrieved, what the agent's step-by-step logic was, and confidence scores for each answer.
- Challenge 4: PII and Sensitive Data Exposure:
- The Risk: AI retrieves HR records containing SSNs, medical data, or salary information and includes it in answers. Even with good intent, this violates GDPR, HIPAA, or CCPA if the requesting user isn't authorized.
- Real Impact:
- GDPR fines for improper data disclosure
- HIPAA violations for PHI exposure
- Insider trading risks from premature financial disclosure
- Docmet's Solution: Automated PII detection and masking. The Compliance Agent scans all responses before delivery and redacts sensitive information based on the requesting user's permissions.

Defense in Depth Architecture:
Security isn't a single feature—it's every feature. Here's how Docmet protects your knowledge at every layer.
- LAYER 1: Identity & Access Management:
- Enterprise SSO Integration: Never manage another password. Docmet integrates with your existing identity provider as the single source of truth.
- Supported Providers:
- Okta
- Azure Active Directory (Microsoft Entra ID)
- Google Workspace
- Ping Identity
- OneLogin
- Generic SAML 2.0
- Features:
- Single Sign-On (SSO): Eliminate separate Docmet passwords
- Multi-Factor Authentication (MFA): Enforce MFA at identity provider level
- Just-In-Time (JIT) Provisioning: Auto-create users on first login
- Automated De-Provisioning: Remove access when employees leave
- Group Sync: Automatically map Azure AD/Okta groups to Docmet teams
- Session Management: Configurable timeout, forced re-authentication
- Result: Your identity provider remains the source of truth. Docmet users are always in sync with HR systems. Terminated employees lose access instantly.
- Available: Growth plan and above
- LAYER 2: Granular Role-Based Access Control (RBAC):
- Permission-Aware AI: Most AI tools have binary access: you're in or you're out. Docmet implements hierarchical, inheritance-based permissions at six levels.
- Permission Hierarchy:
- User Level: Individual access rights
- Team Level: Department or project-based access
- Role Level: Job function-based permissions (Admin, Editor, Viewer)
- Space Level: Workspace-wide permissions
- Folder Level: Collection-level permissions
- Page Level: Document-specific permissions
- Permission Types:
- View: Read document and use in AI queries
- Comment: Add comments and suggestions
- Edit: Modify content
- Share: Grant access to others
- Admin: Manage permissions and settings
- Delete: Remove content (recoverable for 30 days)
- Inheritance Model: Permissions flow down the hierarchy but can be overridden at any level. A Folder can be more restrictive than its Space, and a Page can override its Folder.
- AI-Aware Permissions: When you query the AI, it only retrieves documents you have View access to. If you can't see it, the AI can't use it to answer your questions.
- Available: All plans
- LAYER 3: Encryption & Secure Communication:
- Data Protection at Rest and In Transit: Your data is encrypted everywhere it exists.
- At Rest (Storage):
- Algorithm: AES-256-GCM (industry standard)
- Key Management: Separate encryption keys per tenant
- Database: Encrypted at storage layer (Azure Storage SSE)
- Backups: All backups encrypted with separate keys
- File Storage: Encrypted blob storage with access controls
- Vector Database: Encrypted Qdrant collections
- In Transit (Network):
- Protocol: TLS 1.3 (TLS 1.2 deprecated)
- Certificate Authority: Let's Encrypt with automatic renewal
- Perfect Forward Secrecy: Enabled
- HSTS: Enforced (HTTP Strict Transport Security)
- Certificate Pinning: Available for enterprise mobile apps
- Key Rotation:
- Encryption keys rotated every 90 days automatically
- Zero-downtime key rotation using dual encryption
- Customer-managed keys (CMK) available on Business plan
- Future Enhancement (Q3 2026): Customer-Managed Keys (CMK) allowing you to provide your own encryption keys stored in AWS KMS or Azure Key Vault. You control decryption.
- Available: All plans (CMK on Business+)
- LAYER 4: Tenant Isolation:
- Mathematical Separation: In multi-tenant systems, the biggest risk is cross-tenant data leakage. Docmet's architecture makes this mathematically impossible.
- Database Isolation:
- Separate database schemas per tenant
- No shared tables between tenants
- Query optimizer enforces tenant filters at engine level
- Impossible to write SQL query that crosses tenant boundaries
- Vector Database Isolation:
- Dedicated Qdrant collections per tenant
- Separate vector indexes with unique namespaces
- Similarity search confined to tenant's collection
- Cross-tenant query mathematically impossible
- Knowledge Graph Isolation:
- Separate Neo4j/GraphDB instances per tenant (or separate graphs)
- Entity IDs prefixed with tenant identifier
- Graph traversal confined to tenant subgraph
- Compute Isolation:
- Kubernetes namespace isolation per tenant
- Resource quotas prevent noisy neighbor problems
- Network policies enforce traffic separation
- Result: Company A's document embeddings are invisible to Company B, even at the vector similarity level. No chance of cross-tenant information leakage.
- Available: All plans (enhanced in Business+ with dedicated VPC)
- LAYER 5: PII Masking & Data Loss Prevention:
- Automated Compliance Agent: Before any AI response reaches you, it passes through our Compliance Agent—a specialized system that detects and redacts sensitive data.
- Detection Methods: Pattern-Based (Regex):
- Social Security Numbers (SSN)
- Credit card numbers (PAN)
- Email addresses
- Phone numbers
- IP addresses
- Driver's license numbers
- ML-Based (Fine-Tuned NER):
- Personal names (PERSON entities)
- Physical addresses (LOCATION entities)
- Medical record numbers
- Salary and compensation data
- Bank account numbers
- Action Taken: Sensitive data is replaced with tokens before display:
- `[SSN_REDACTED]`
- `[EMAIL_MASKED]`
- `[SALARY_PROTECTED]`
- Audit Trail: Original unmasked data is logged (encrypted) for compliance audits but never displayed to unauthorized users or sent to LLMs.
- Configurable: Admins can configure which PII types to mask and define custom patterns for proprietary identifiers (product codes, customer IDs).
- Available All plans
- LAYER 6: Complete Audit Trail:
- Immutable Activity Logging: Every action in Docmet is logged to an append-only audit log. Nothing can be hidden or deleted.
- Events Logged:
- User Events:
- Login, logout (with IP address and user agent)
- Password reset attempts
- Permission changes
- Role assignments
- Account settings modifications
- Data Access:
- Document viewed (page ID, timestamp, duration)
- File downloaded (file hash, size)
- Page edited (diff of changes)
- Content deleted (soft delete, recoverable)
- Search queries executed
- AI Queries:
- Full query text
- Retrieved documents (IDs and relevance scores)
- Agent reasoning steps
- Generated response
- Confidence scores
- Processing time
- Administrative Actions:
- User provisioning/de-provisioning
- Permission grants/revocations
- Configuration changes
- Integration enablement
- API key generation
- Log Format:
- Each log entry includes:
- Timestamp UTC with millisecond precision
- User ID Who performed the action
- IP Address Where the request originated
- Session ID Link to authentication session
- Action Type Categorized event
- Resource ID What was accessed/modified
- Result Success/Failure with error codes if applicable
- User Agent Browser/API client information
- Storage & Retention:
- Write-Only Log Append-only (cannot be modified or deleted)
- Retention Configurable (default 7 years for compliance)
- Export Stream to Splunk, Datadog, Elasticsearch, or S3 via API
- Search Full-text search within audit log interface
- Alerts Configurable alerts for suspicious patterns
- Available All plans (export API on Growth+)

DEPLOYMENT OPTIONS
Flexibility to Match Your Security Requirements: Choose the deployment model that aligns with your security policies—from fully managed SaaS to completely air-gapped infrastructure.
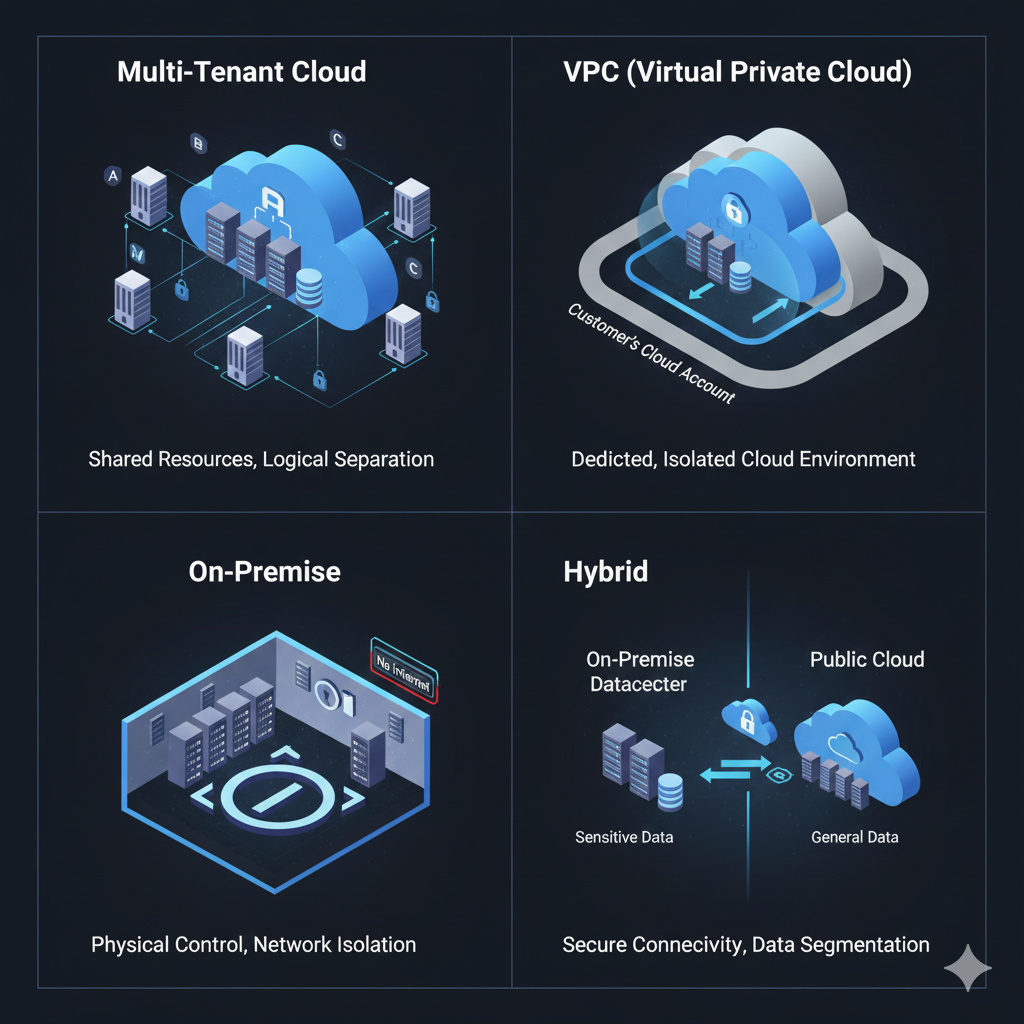
OPTION 1: Multi-Tenant Cloud (Standard SaaS):
- Best For: Small to mid-size businesses, departmental deployments
- Infrastructure:
- Shared Kubernetes cluster on Azure
- US East region (with EU West option for GDPR)
- Logical tenant separation via database schemas and namespaces
- Isolation Level: Logical separation (dedicated DB, vectors, graphs)
- Security Features:
- All six security layers active
- SOC2 Type II compliant (in progress)
- GDPR compliant with data residency options
- 99.5% uptime SLA
- Setup Time: Instant (self-service signup)
- Pricing: Starter ($49/mo) or Growth ($149/mo) plans
- Available: All customers
OPTION 2: Single-Tenant Cloud (Private VPC):
- Best For: Regulated industries (Finance, Healthcare, Legal)
- Infrastructure:
- Dedicated Kubernetes cluster in your AWS or Azure subscription
- Your Virtual Private Cloud (VPC)
- Physical tenant separation—your data never touches shared infrastructure
- Isolation Level: Complete infrastructure isolation
- Security Features:
- Everything in Multi-Tenant
- Custom VPC peering configurations
- Private endpoints (no public internet exposure)
- Dedicated IP addresses with allowlist support
- Customer-managed encryption keys (CMEK)
- Custom network policies and firewall rules
- Dedicated monitoring and alerting
- Compliance:
- Meets financial services data residency requirements
- HIPAA-ready architecture (BAA required)
- FedRAMP Moderate pathway (roadmap)
- Setup Time: 2-4 weeks (includes infrastructure provisioning and security review)
- Pricing: Business plan ($499/mo) + $800/mo VPC management fee + $15,000 setup
- Available: Business plan and above
OPTION 3: On-Premise / Air-Gapped:
- Best For: Government, defense, zero-trust environments
- Infrastructure:
- Complete Dockerized Docmet stack
- Deployed on your on-premise servers or private cloud
- No internet access required (complete air-gap)
- Isolation Level: Complete physical and network isolation
- Components Included:
- Self-hosted LLMs (Llama 3, Mistral, or your custom models)
- Local Qdrant vector database
- Neo4j/GraphDB knowledge graph server
- PostgreSQL/MySQL relational database
- Web application and agent orchestration services
- Offline documentation and troubleshooting guides
- Security Features:
- Everything in VPC
- Zero external network dependencies
- Air-gapped update delivery mechanism (secure USB or internal transfer)
- Hardware security module (HSM) integration available
- Offline authentication (local LDAP/AD)
- Custom security hardening per your policies
- Compliance:
- ITAR compliant deployment available
- IL5 (Impact Level 5) compatible
- Meets CMMC Level 3 requirements
- Setup Time: 6-8 weeks (infrastructure setup, security review, testing)
- Pricing: $95,000 setup + custom annual licensing (based on user count and capacity)
- Available: Enterprise contracts only
OPTION 4: Hybrid Architecture:
- Best For: Large enterprises with mixed data sensitivity
- Architecture:
- Sensitive data (HR, Finance, Legal) remains on-premise
- General knowledge (Marketing, Engineering docs, Product) in cloud
- Unidirectional sync (cloud cannot pull from on-premise, only receive pushes)
- Use Case Example:
- Employee handbook: On-premise (contains SSNs, salaries)
- Product documentation: Cloud (needs broad access)
- Query across both: "What's our parental leave policy?" → retrieves from on-premise
- Security Features:
- Encrypted tunnel between environments
- Data classification and routing rules
- Separate permission systems with inheritance
- Cross-environment audit logging
- Setup Time: 10-12 weeks (custom architecture design and deployment)
- Pricing: Custom quote based on complexity
- Available: Enterprise contracts only
COMPLIANCE & CERTIFICATIONS
Built to Meet Global Regulatory Standards: Compliance isn't optional in enterprise AI. Docmet is designed from the ground up to meet the strictest regulatory requirements.
SOC2 Type II:
- Status: Audit in progress, completion Q2 2026
- Scope: Security, Availability, Confidentiality, Processing Integrity
- Controls:
- 200+ control objectives across
- Infrastructure security
- Access management
- Change management
- Incident response
- Business continuity
- Data protection
- Vendor management
- Audit Firm: [Top 4 Accounting Firm]
- Annual Re-Audit: Required to maintain certification
- Customer Access: SOC2 report provided under NDA to qualified prospects and Business+ customers
- What This Means: Independent verification that Docmet's controls are designed appropriately and operating effectively to protect customer data.
GDPR (General Data Protection Regulation):
- Status: Fully compliant
- Capabilities:
- Data Processing Agreements (DPA):
- Signed DPAs with all customers processing EU data
- Sub-processor agreements with LLM providers (OpenAI, Anthropic)
- Controller-to-Processor relationship documented
- Individual Rights:
- Right to be Forgotten: Delete user data on request (within 30 days)
- Data Portability: Export all data in structured JSON format
- Right to Access: User dashboard showing all stored data
- Right to Rectification: Users can correct inaccurate data
- Right to Restrict Processing: Temporary processing halt available
- Privacy by Design:
- Data minimization (collect only necessary data)
- Purpose limitation (use data only for stated purposes)
- Storage limitation (automatic deletion after retention period)
- Breach Notification: Within 72 hours to supervisory authority and affected users
- Data Residency: EU customers can choose EU-West Azure region for data storage
- DPO: Designated Data Protection Officer available at [email protected]
- Subprocessors: Published list of all third-party services with data access
HIPAA (Health Insurance Portability and Accountability Act):
- Status: HIPAA-ready, BAA available
- Eligibility: Business plan and above with signed Business Associate Agreement
- Features:
- PHI Protection:
- Protected Health Information (PHI) detection and masking
- Encrypted storage (AES-256) and transmission (TLS 1.3)
- Access logs for all PHI access
- Role-based access to medical records
- Audit trail showing who accessed patient data
- Administrative Safeguards:
- HIPAA training for all staff with PHI access
- Designated Security Officer
- Workforce clearance procedures
- Security incident response plan
- Technical Safeguards:
- Unique user identification
- Automatic logoff
- Encryption and decryption
- Audit controls
- Implementation Requirements:
- Customer must configure RBAC to restrict PHI access to authorized roles
- Customer must designate which data contains PHI
- Customer responsible for user training
- Use Cases: Healthcare providers managing patient records, clinical documentation, research data
ISO 27001:
- Status: Roadmap for 2026
- Scope: Information Security Management System (ISMS) covering all aspects of data handling
- Benefits:
- Demonstrates systematic approach to managing sensitive data
- Required by many enterprise procurement processes
- International recognition
- Timeline: Certification expected Q4 2026
CCPA / CPRA (California Privacy Rights):
- Status: Fully compliant
- Capabilities:
- User data deletion on request
- Opt-out of data sales (we don't sell data—automatic compliance)
- Transparency reports on data usage
- Right to know what data is collected
- Non-discrimination for exercising rights
- Applicability: Automatically compliant—our practices exceed CCPA requirements
Additional Compliance Support:
- FedRAMP (Roadmap): Federal Risk and Authorization Management Program certification planned for government customers. Moderate baseline expected 2027.
- PCI DSS: Payment Card Industry Data Security Standard—relevant if storing payment card data. Currently not in scope (payment processing via Stripe).
- ITAR: International Traffic in Arms Regulations compliance available for defense contractors via on-premise deployment.

SECURITY TESTING & VALIDATION
Continuous Security Assessment: We don't just claim security—we prove it through rigorous, ongoing testing.
Penetration Testing:
- Frequency: Annual third-party penetration tests
- Scope:
- Application security (OWASP Top 10)
- Infrastructure security (network, servers, databases)
- Authentication and authorization
- API security
- Social engineering assessment
- Testing Firm: [Leading cybersecurity firm]
- Methodology: Black-box, gray-box, and white-box testing
- Remediation: All critical and high findings remediated within 30 days
- Customer Access: Business+ customers can request pen test report under NDA
- Custom Testing: Enterprise customers may conduct their own pen tests with prior written approval and scoping agreement
Vulnerability Management:
- Continuous Scanning:
- Automated vulnerability scanning (weekly)
- Dependency checking (daily)
- Container image scanning (on every build)
- Open-source component monitoring
- Patch Management:
- Critical vulnerabilities patched within 24 hours
- High vulnerabilities patched within 7 days
- Medium/Low vulnerabilities addressed in regular maintenance windows
- Bug Bounty Program: Launching Q2 2026—security researchers can report vulnerabilities for rewards
Security Monitoring:
- 24/7 Monitoring:
- SIEM integration (Splunk, Datadog)
- Real-time threat detection
- Anomaly detection via ML
- DDoS protection and mitigation
- Incident Response:
- Dedicated security incident response team
- <30 minute response time for critical incidents (Business plan)
- Post-incident reports provided to affected customers
DATA PROCESSING & PRIVACY
Transparent Data Handling: You own your data. We're just trusted stewards.
Data Ownership:
- Principle: You retain all rights, title, and interest in your data
- Our Rights: Limited license to process data solely to provide services
- No Training: We never use your data to train AI models. Period.
- Data Processing Agreements: All LLM providers (OpenAI, Anthropic, Mistral) have strict DPAs prohibiting training on customer data.
Data Collection:
- What We Collect:
- Account Data:
- Email address, name, company name
- Billing information (processed by Stripe, not stored by us)
- SSO identity provider details
- Content Data:
- Documents, pages, comments you create
- Search queries and AI interactions
- Usage patterns and analytics
- Technical Data:
- IP addresses, user agents
- Session information
- Performance metrics
- What We Don't Collect:
- We don't track you across other websites
- No third-party advertising cookies
- No selling data to data brokers
Data Retention:
- Active Data: Retained while you're an active customer
- Deleted Data:
- Soft delete: 30-day recovery period
- Hard delete: Permanent removal after 30 days
- Backups: Removed from backups within 90 days
- Audit Logs: Retained for 7 years (configurable) for compliance purposes
- Account Closure: All data permanently deleted within 90 days of account termination (unless legal hold applies)
Data Portability:
- Export Options:
- Export all content as JSON, Markdown, or PDF
- Bulk download via API
- Database dumps available for Enterprise customers
- No Lock-In: You can always export your data and migrate to another system
RESPONSIBLE DISCLOSURE & SECURITY ROADMAP
Working With Security Researchers: We believe in collaborative security. If you discover a vulnerability, we want to hear from you.
Reporting Security Issues:
- Email:** [email protected]
- PGP Key: [Provided on security page]
- What to Include:
- Detailed description of the vulnerability
- Steps to reproduce
- Potential impact
- Your contact information
- Response Timeline:
- Initial response: Within 24 hours
- Status update: Within 7 days
- Resolution target: 30-90 days (depending on severity)
Responsible Disclosure Policy:
- Our Commitments:
- We will not pursue legal action against researchers who follow responsible disclosure
- We will acknowledge researchers (with permission) in our security hall of fame
- We will keep researchers updated on remediation progress
- Researcher Responsibilities:
- Do not access or modify data beyond what's necessary to demonstrate the vulnerability
- Do not disrupt our services
- Give us reasonable time to fix issues before public disclosure
- Do not publicly disclose vulnerabilities until we've had time to remediate
- Bug Bounty Program: Launching Q2 2026 with rewards for qualifying vulnerabilities
Continuous Security Investment: Security isn't static. Here's what's coming.
- Q2 2026: Customer-Managed Keys (CMK): Enterprise customers can provide their own encryption keys stored in AWS KMS or Azure Key Vault. You control decryption—we can't access your data without your keys.
- Q3 2026: Bug Bounty Program: Public bug bounty program via HackerOne or Bugcrowd. Reward security researchers who help us improve.
- Q4 2026: Confidential Computing: Deploy AI workloads in Azure Confidential VMs with Intel SGX enclaves. Data encrypted even during processing in CPU memory.
- 2027: Blockchain Audit Trail (Optional): Immutable audit log on blockchain (Hyperledger) for ultimate tamper-proof compliance evidence. Useful for highly regulated industries requiring cryptographic proof of audit integrity.
How Docmet Stacks Up Against Generic AI Tools
FREQUENTLY ASKED QUESTIONS
We've designed every component of Docmet with security as the primary requirement. From encryption to isolation to audit trails, your knowledge is protected at every layer.
Schedule a 60-minute security deep-dive with our CISO team. We'll walk through our architecture, compliance certifications, and answer your specific security questions. Security architecture walkthrough - Compliance certification review - Answers to your security questionnaire - Penetration test results (under NDA) - Custom deployment recommendations